Spiderfoot OSINT taught me more in 10 minutes than an entire week of googling.
The first time I realized how much information I was leaking online, it wasn’t during a cybersecurity talk or while reading a privacy blog. It was when someone reverse-engineered my email signature, pieced together my domain history, and casually mentioned my old freelance site—one I hadn’t touched in years.
That rabbit hole? It started with Spiderfoot OSINT.
I had installed it on a whim, curious about what it could dig up. What I found was unsettling: domain registrations, social media breadcrumbs, even the ghost of an old username tied to a throwaway forum post. All indexed. All connected.
The best part? It’s open source. No hidden strings. No “pro version” gatekeeping the features that matter.
If you’re running Linux or Mac and want to get Spiderfoot OSINT up and scanning in minutes—without Docker, without fuss—you’re in the right place.
Let’s set it up, dig in, and see what the web has to say about you.
⚠️ Important: These tools are intended for ethical hacking, security research, and education. Use them only on systems and networks you own or have permission to test. Unauthorized use can lead to serious legal consequences.
- What Is Spiderfoot OSINT (and Why You Should Care)
- How to Install Spiderfoot OSINT on macOS and Ubuntu (The Right Way)
- Common Spiderfoot OSINT Scans (and What They Reveal)
- Spiderfoot Limitations: What It Can’t (or Shouldn’t) Do
- Troubleshooting Spiderfoot: When Things Break (and They Will)
- Wrapping Up: What Spiderfoot Sees, You Can’t Unsee
What Is Spiderfoot OSINT (and Why You Should Care)
A Swiss Army Knife for Open Source Intelligence
Spiderfoot OSINT is a powerful, open source reconnaissance tool that automates the collection and correlation of public data—metadata, IPs, usernames, domains, leaks, and more. With over 200 modules, it connects the dots between seemingly random bits of information to build a surprisingly complete digital profile of a target.
Whether you’re a penetration tester, digital forensics analyst, or privacy-conscious individual, Spiderfoot offers a GUI-free way to surface what the internet quietly knows about you—or someone else.
Best Run on Desktop Linux or macOS
While Spiderfoot can technically be installed on any system that supports Python, its best performance and reliability come from full Linux distributions and macOS systems.
These platforms offer better Python dependency handling, broader module compatibility, and fewer permission issues during scans.
A Word About Termux: Not Ideal for Spiderfoot
Yes, it’s possible to force Spiderfoot to run on Termux. But in practice, it’s clunky. You’ll run into:
- Broken dependencies
- Python module conflicts
- Web UI launch issues
- And some modules just… won’t work.
If you’re serious about using Spiderfoot for real OSINT work, stick to a VM, server, or local dev machine running Ubuntu, Debian, Arch, or macOS.
Real-World Use Cases
Spiderfoot isn’t just a toy for infosec hobbyists. Here’s where it shines:
- Digital footprint discovery – See what an attacker can learn about you in 10 minutes.
- Username correlation – Find where a username pops up across domains and leaks.
- Threat intelligence – Map domains, IPs, ASN records, and potential phishing connections.
- Due diligence – Vet a vendor, client, or applicant using only open data sources.
- Red teaming – Use Spiderfoot to simulate what a passive recon phase looks like.
In short, Spiderfoot OSINT is what happens when you give open source tools the power—and the purpose—of professional-grade recon.
· · ─ ·𖥸· ─ · ·
How to Install Spiderfoot OSINT on macOS and Ubuntu (The Right Way)
While Spiderfoot OSINT is built in Python and technically cross-platform, not all installation paths are created equal. If you’ve ever fought with missing dependencies or broken modules, you know the pain.
This guide uses a Python virtual environment to keep things clean, reproducible, and conflict-free—whether you’re on macOS or Ubuntu. No Docker, no dirty system-wide installs. Just a lean, focused setup that works.
Installation for macOS
Tested on macOS Monterey and Ventura. Assumes Homebrew is installed.
Install dependencies:
brew install python3 gitClone Spiderfoot:
git clone https://github.com/smicallef/spiderfoot.git
cd spiderfootCreate and activate a virtual environment:
python3 -m venv venv source venv/bin/activateInstall requirements:
pip install --upgrade pip pip install -r requirements.txtRun Spiderfoot with the web UI:
python3 sf.pyAccess the interface:
Open your browser and go to http://localhost:5001
Installation for Ubuntu (Debian-based)
Tested on Ubuntu 22.04. Assumes you have
sudoprivileges.
Update packages and install dependencies:
sudo apt update sudo apt install -y python3 python3-pip python3-venv gitClone Spiderfoot:
git clone https://github.com/smicallef/spiderfoot.git cd spiderfootCreate and activate a virtual environment:
python3 -m venv venv source venv/bin/activateInstall requirements:
pip install --upgrade pip pip install -r requirements.txtLaunch Spiderfoot: bashCopyEdit
python3 sf.pyAccess the web UI:
Navigate to http://localhost:5001 in your browser.
· · ─ ·𖥸· ─ · ·
Common Spiderfoot OSINT Scans (and What They Reveal)
Spiderfoot isn’t just about running a scan—it’s about surfacing hidden relationships and context buried in public data. With the right modules, a single scan can uncover everything from forgotten domains to exposed credentials. The magic is in the modules you enable—and knowing what they’re good for.
Whether you’re doing recon for security testing or self-auditing your digital exposure, here are some of the most common and valuable Spiderfoot scans.
Domain or IP Scan
What it does:
Uncovers DNS records, WHOIS data, server metadata, hosting providers, subdomains, and more.
Why it matters:
You get a full picture of the attack surface—often including assets you forgot existed. Great for mapping infrastructure during red-teaming or assessing shadow IT risks.
Username Scan
What it does:
Checks if a given username is used across dozens of platforms (social media, forums, developer sites, etc.).
Why it matters:
Excellent for tracking digital aliases, deanonymizing targets, or spotting old accounts tied to your brand, alias, or identity. Especially useful when paired with OSINT tools like Sherlock or Maigret.
Phone Number Scan
What it does:
Searches for data breaches, leak dumps, spam reports, social media traces, and associations with domains or public identities.
Why it matters:
Reveals whether a number is part of a known scam, reused in shady operations, or tied to suspicious online activity. Crucial for fraud detection, threat intel, or vetting unknown contacts.
Email Address Scan
What it does:
Searches for breaches, leak dumps, PGP keys, associated domains, and public mentions of the email.
Why it matters:
Exposes whether your email has been compromised, reused across services, or unintentionally indexed online. Eye-opening for privacy audits and breach forensics.
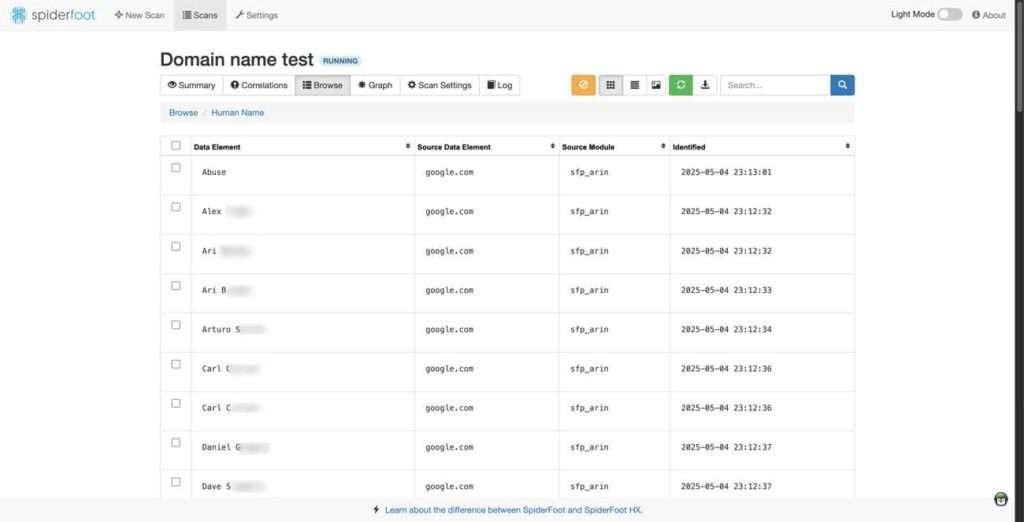
Human Name Scan
What it does:
Looks for references to full names across web sources, breaches, and structured data.
Why it matters:
Helps map a digital identity and find potential exposures in forums, leak sites, or public records—useful for investigative journalism, HR due diligence, or privacy-conscious individuals.
Custom Word or Keyword Scan
What it does:
Searches for specific words across indexed datasets, public sources, and dark web aggregators.
Why it matters:
Good for brand monitoring, sensitive term auditing, or tracking mentions of unique aliases, projects, or leaks.
Each scan is modular—you can fine-tune which data sources to include, how aggressively Spiderfoot scrapes, and how results are displayed. You’re not just seeing what’s out there, you’re seeing how the dots connect.
· · ─ ·𖥸· ─ · ·
Spiderfoot Limitations: What It Can’t (or Shouldn’t) Do
Spiderfoot is a powerful tool, but like all OSINT frameworks, it has its boundaries—and understanding them can save you time, confusion, or a failed scan at 2 AM.
First, it’s only as good as its modules and sources. If a site blocks scraping or changes its structure, Spiderfoot might miss data or throw an error. Some sources require API keys, and without them, results will be incomplete. Also, expect false positives—especially when scanning common usernames or domains. Spiderfoot casts a wide net, not a sniper rifle.
Another real-world limitation: speed. Deep scans can take hours or choke when you enable too many modules. And while it works on Mac and Linux, lightweight systems (like Termux on Android) are prone to crashes, dependency issues, or failed installations due to missing packages.
Finally, there’s context. Spiderfoot pulls data, but it doesn’t explain it. Interpretation is up to you—and that’s where real OSINT skill kicks in.
· · ─ ·𖥸· ─ · ·
Troubleshooting Spiderfoot: When Things Break (and They Will)
Let’s be honest: Spiderfoot is not immune to install quirks, broken modules, or API tantrums. If you’re hitting snags, you’re not alone. Here’s how to fix common issues fast.
Missing or Broken Modules
Some modules rely on external APIs or web scraping. If scans silently fail or return nothing, check the module config. Did you provide an API key? Is the target site online? Has the source changed its layout?
Fix: Disable modules that aren’t critical. Update Spiderfoot. Reinstall broken dependencies.
Installation Fails or Crashes
If you’re on Mac or Ubuntu and the installation hangs or crashes, it’s often due to missing Python packages or environment conflicts.
Fix:
Use a virtual environment:
python3 -m venv venv && source venv/bin/activate
pip install -r requirements.txtAvoid using Termux unless you’re okay with chasing obscure errors.
Slow or Frozen Scans
If scans crawl or hang, you’ve likely enabled too many heavy modules, or your network is choking.
Fix:
Start with fewer modules. Run from a stable machine with good bandwidth. Monitor RAM and CPU usage if Spiderfoot starts to freeze mid-scan.
Web UI Not Loading
If the web interface fails to load on http://127.0.0.1:5001, check that the Spiderfoot process is running.
Fix:
Make sure you’re running the tool in the correct virtual environment and port isn’t in use. Restart with:
python3 sf.py -l 127.0.0.1:5001· · ─ ·𖥸· ─ · ·
Wrapping Up: What Spiderfoot Sees, You Can’t Unsee
Once you’ve fired off your first Spiderfoot scan, it’s hard to look at the internet the same way. Every link is a lead. Every email address, a potential map. And every time you think, “Nah, nobody would care about that,” Spiderfoot quietly reminds you that yes—yes, they would.
In this guide, we covered how to get Spiderfoot OSINT running quickly on Linux and Mac, all with a FOSS-first approach. No proprietary fluff. Just powerful open-source intelligence at your fingertips.
Want more practical, no-BS guides on open source tools, privacy, and ethical hacking?
Subscribe to my newsletter — it’s where I share the real gems I don’t post anywhere else.














Leave a Reply