Geotagging isn’t just for hackers in hoodies—it’s how I stayed online coding in the foggy cliffs of Sagada, without leaking signal or getting lost.
WiFi in the Wild—And Why I Started Geotagging Signals
Between 2017 and 2019, I lived like many idealistic software developers dream of—off-grid but online, high up in the cool pine forests of Sagada, Mountain Province. I wrote code by day and drank strong barako by night, surrounded by limestone cliffs, rice terraces, and the soft hum of adventure.
But life as a digital nomad teaches you one brutal truth early: without a stable internet connection, your productivity goes as dead as the local telco’s customer support line.
In Sagada, the signal waxes and wanes like the moon. Near the caves, your bars disappear into the rock. On the trail to Bomod-ok Falls? Good luck. Local cafés and hostels generously offered WiFi—bless them—but remembering which spot had the least packet loss at 7PM became a game of chance.
That’s when I turned to geotagging WiFi networks. It wasn’t just a clever hack—it became a survival skill. Using only open-source tools, a phone, and GPS, I started building a digital map of accessible hotspots: who had the best signal, which routers reached beyond their walls, and where I could tuck myself in for a full sync session.
What began as a way to find WiFi in the mountains became a serious lesson in ethical wardriving—with major implications for privacy, open access, and even network defense.
Want to learn how to build your own WiFi geotagging toolkit for ethical recon? Read on.
- WiFi in the Wild—And Why I Started Geotagging Signals
- What Is WiFi Geotagging?
- Why Geotag WiFi Networks? (And What You’ll Gain)
- Why Wigle WiFi Is the Logical Choice
- How to Install and Use Wigle WiFi
- Comparing Other Geotagging Methods
- What to Do After You’ve Collected WiFi Geotagging Data
- Download Your Wigle KML or CSV Data
- Integrate with Your Own GIS or Recon Database
- Generate Heatmaps of Signal Density
- Tabulate Internet Service Providers in Urban Areas
- Detect Open, Misconfigured, or Unusual Networks
- Bundle and Share with Local NGOs or Tech Advocates
- Create Visual Reports for Stakeholders
- Real-World Uses of WiFi Geotagging
- Wrapping Up: From Pine Trees to Packet Traces
What Is WiFi Geotagging?
WiFi geotagging is the process of mapping wireless access points by combining their signal data with GPS coordinates. Think of it as “wardriving with a purpose”—you’re collecting network visibility data and logging where each WiFi signal appears on a map.
This is not about cracking passwords or breaking in. It’s about understanding wireless terrain for network diagnostics, ethical recon, and informed defense—especially critical when working in open environments or insecure areas.
With the right open-source tools, you can scan for SSIDs, MAC addresses, channel use, and signal strength, then pair that with GPS data to visualize hotspots, leaks, or threats.
Like what you’re reading?
Help keep DevDigest
free and caffeine-powered
—buy me a coffee on Ko-fi.
Why Geotag WiFi Networks? (And What You’ll Gain)
Geotagging gives you a unique tactical edge in environments where digital infrastructure overlaps with public spaces. Here’s what it offers:
- Network Visibility — See what routers broadcast where, even beyond building walls
- Security Awareness — Identify rogue APs, signal leakage, or misconfigured hotspots
- Operational Advantage — Pinpoint reliable access points in rough terrain or urban dead zones
- Free Open-Source Toolkit — Do it all using FOSS tools on Android or Linux devices
Whether you’re a field researcher, penetration tester, NGO worker, or just someone working out of a mountain shack (been there), this gives you power and insight with minimal gear.
· · ─ ·𖥸· ─ · ·
Why Wigle WiFi Is the Logical Choice
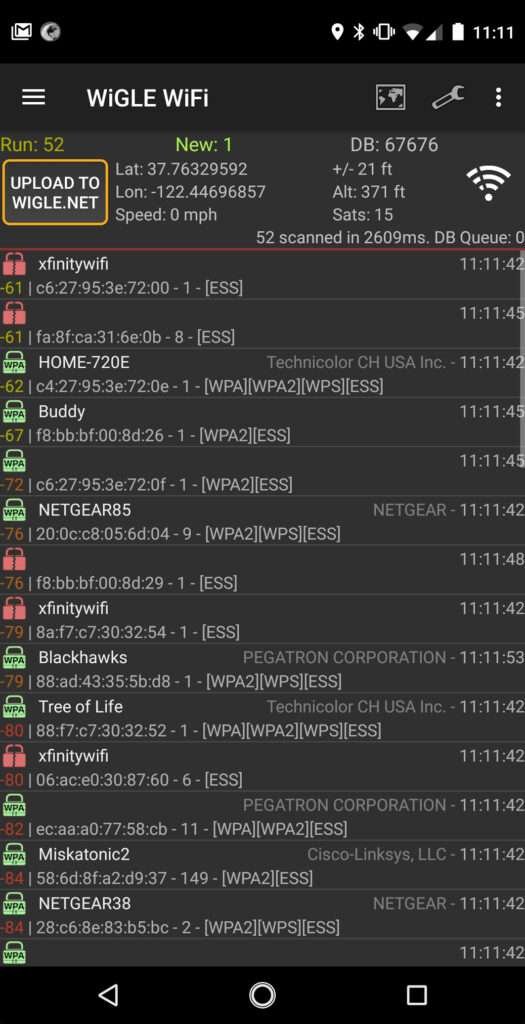
If you’re new to WiFi geotagging or just want to get up and running fast, Wigle WiFi is the most efficient, ethical, and user-friendly option. The Android app combines GPS and WiFi scanning to map networks around you in real-time, logging everything from SSIDs to encryption status and MAC addresses.
Why it stands out:
- Built-in GPS logging
- Automatic logging of visible WiFi networks
- Visual heatmap of scanned areas
- Optional uploads to a global open database
- Export to CSV and KML via website
- Covert
- Portable
Plus, the app is FOSS-friendly: while the Android client itself is closed source, the data model and community encourage open access and collaboration. You can choose to contribute to the global dataset—or keep your logs entirely local.
· · ─ ·𖥸· ─ · ·
How to Install and Use Wigle WiFi
Note: Wigle WiFi only works on Android. iPhone users, you’re out of luck unless you jailbreak (not recommended).
Step 1: Install the App
- Download Wigle WiFi Wardriving from the Google Play Store.
Step 2: Create an Account (Optional but Recommended)
- Go to https://wigle.net and create an account.
- This lets you upload data, generate maps, and export geotagged logs from your dashboard.
Step 3: Start Scanning
- Launch the app and grant GPS + location permissions.
- Tap the scan button. As you move, the app automatically logs all visible WiFi networks.
- You can view basic maps within the app, or upload later to explore in detail on the website.
Step 4: Export Your Logs
- After syncing data to the Wigle servers, log in at wigle.net from a desktop browser.
- Go to your Stats > Observations.
- Use filters to narrow down a location or time.
- Export to CSV or KML for use in your own mapping or recon tools.
· · ─ ·𖥸· ─ · ·
Comparing Other Geotagging Methods
Here’s a quick breakdown of alternative ways to do WiFi geotagging, if you prefer more control or want to scale:
| Method | Pros | Cons |
|---|---|---|
| Wigle WiFi App | – Easy to use (Android) – GPS integration built-in – Exports to CSV/KML via web UI – Contributes to global mapping project | – Requires account and upload – No export from app directly – Closed source – May raise privacy concerns |
| Airodump-ng + GPSD | – CLI-based, great control – Logs to CSV + GPS – Works with gpsd and external GPS | – Manual setup – Not beginner-friendly – CSV needs parsing or post-processing |
| Kismet | – Beautiful web UI – Real-time mapping – Supports many radios and GPS – Export to multiple formats | – Resource-intensive – Can crash low-power systems – Steeper learning curve |
| Scapy + GPS Script | – Fully customizable – Fine-tuned data capture – Great for learning | – Coding knowledge required – No UI – Must build your own exporter |
| WiFiDB (self-hosted) | – Private, secure – Easy CSV upload – Map-based interface – FOSS | – Requires LAMP stack – No mobile app – Manual upload process |
Like what you’re reading?
Help keep DevDigest
free and caffeine-powered
—buy me a coffee on Ko-fi.
What to Do After You’ve Collected WiFi Geotagging Data
Once your Android has done its part collecting geotagged WiFi data, it’s time to transform that data into something useful. These steps walk you through post-processing, analysis, and ethical application of your reconnaissance work.
Download Your Wigle KML or CSV Data
After uploading your data to Wigle, visit your Wigle.net account to export it in the format you need.
- Why it matters:
- KML is ideal for use in mapping applications like Google Earth or QGIS.
- CSV is best for spreadsheets, databases, or writing scripts to parse and analyze data.
- FOSS Tip:
Use a Python script withpandasto clean and sort CSV exports.
Integrate with Your Own GIS or Recon Database
Feed your data into a Geographic Information System (GIS) or a lightweight database for deeper insight.
- Tools you can use:
QGIS, Leaflet.js, PostGIS, SQLite - Use case:
Identify hotspots, coverage gaps, or overlapping signals that might indicate misconfigured or clustered APs.
Generate Heatmaps of Signal Density
Turn signal strength and network density into visual insight.
- Tools and workflows:
QGIS heatmap plugins, Google Earth Pro, Folium + Python - Use case:
Understand which locations are rich in connectivity and where digital blackouts still exist.
Tabulate Internet Service Providers in Urban Areas
Analyze MAC address prefixes (OUIs) to determine ISP identity or manufacturer.
- Steps:
Parse BSSIDs → extract first 6 characters → lookup OUI - Why this matters:
Useful for advocacy or policy analysis—especially to detect monopolies or underserved areas.
Detect Open, Misconfigured, or Unusual Networks
Review logs for unsecured or suspicious SSIDs.
- Signs to look for:
Default SSIDs (e.g., TP-LINK_XXXX), Repeated MACs, Open networks in odd locations - Ethical note:
Never connect or tamper. Use findings for education, advocacy, or responsible disclosure.
Bundle and Share with Local NGOs or Tech Advocates
Format your data and maps to be usable by other changemakers.
- Output formats:
Clean CSVs, PNG map snapshots, KML overlays, GeoJSON - Use case:
Support groups working on rural internet, education access, or disaster relief.
Create Visual Reports for Stakeholders
Translate raw data into reports decision-makers can understand.
- Key visuals:
Encryption stats, ISP presence maps, Time-based network changes - Tools:
LibreOffice, Jupyter Notebooks, Chart.js, Google Charts
Real-World Uses of WiFi Geotagging
For NGOs and Advocacy Groups
- Map rural WiFi hotspots to identify digital deserts
- Ensure safe, limited-range APs in women’s shelters or sensitive operations
- Audit donated routers to validate coverage areas
For Government and Community Networks
- Survey public WiFi rollouts (e.g. barangay or city hotspots)
- Check for interference or signal overlap in dense areas
- Assist in disaster recovery mapping for emergency comms
For Businesses
- Detect unauthorized repeaters or rogue APs in office parks or retail spaces
- Validate router placement and adjust for maximum signal efficiency
- Monitor and secure client WiFi zones like cafés or coworking spaces
For Students, Techies, and Bloggers
- Learn how real-world wireless environments behave
- Build security awareness and technical reporting skills
- Use it as a foundation for blogs, podcasts, or academic work on network security
· · ─ ·𖥸· ─ · ·
Wrapping Up: From Pine Trees to Packet Traces
A Practical FOSS Recon Tool That Starts With Curiosity
What began as a desperate search for WiFi in the mountains became a lifelong respect for the power of network visibility. Geotagging is more than just a fun technical exercise—it’s a practical tool for digital nomads, ethical hackers, and defenders alike.
If you’re just getting started, Wigle WiFi is the quickest, simplest, and most intuitive entry point into the world of wireless mapping. And once you’re hooked, the FOSS ecosystem is waiting to offer even deeper tools and more refined methods.
Curious where this rabbit hole leads? Want more tutorials, code samples, and personal stories like this one?
👉 Subscribe now to https://www.samgalope.dev/newsletter/ and level up your toolkit the ethical way
Like what you’re reading?
Help keep DevDigest
free and caffeine-powered
—buy me a coffee on Ko-fi.










Leave a Reply