Search for PDFs like an ethical hacker—not a Google rookie.
It started with a single PDF.
While helping a local NGO audit their online footprint, I stumbled across an old internal document—indexed by Google and forgotten by its creators. It wasn’t locked down.
No password.
No watermark.
Just sitting there, one search away from public eyes.
That’s when I realized just how much sensitive data hides in PDFs, casually exposed by misconfigured web servers and poor digital hygiene.
As an open source advocate, this was both a wake-up call and an opportunity. Tools like Metagoofil—combined with smart search queries—offer a FOSS-friendly, CLI-based way to ethically search for PDFs across domains and domains.
No gimmicks. Just intelligent recon, the kind that can help journalists, IT admins, and transparency watchdogs alike.
So if you’re curious how ethical hackers spot those digital breadcrumbs or want to sharpen your OSINT chops using open tools, read on.
⚠️ Important: These tools are intended for ethical hacking, security research, and education. Use them only on systems and networks you own or have permission to test. Unauthorized use can lead to serious legal consequences.
Meet Metagoofil: Your Recon Ally to Search for PDFs on Any Website
Metagoofil is an open-source intelligence (OSINT) tool designed to help ethical hackers, researchers, and investigators find and download publicly available documents from target domains. Originally created for metadata extraction, modern versions of Metagoofil now focus exclusively on indexing and retrieving documents—like PDFs, DOCs, and PPTs—for deeper offline analysis using tools like exiftool.
It automates a tedious process: manually searching for PDFs (or other docs) hidden deep inside corporate websites, academic portals, or government pages. Think of it as your search-savvy assistant—quietly crawling and listing exposed files you didn’t know were accessible.
· · ─ ·𖥸· ─ · ·
Why Search for PDFs with Metagoofil?
Here’s why Metagoofil is a must-have in your OSINT toolkit:
- Laser-focused automation: No need to craft complex Google dorks or comb through search results—Metagoofil automates the discovery.
- File-type precision: Target only what you need—PDFs, DOCs, PPTs, XLSX, and more.
- Safe for passive recon: No intrusive behavior or website scanning. It sticks to search engine results.
- Offline analysis-ready: Pair with
exiftoolfor powerful metadata extraction after download.
From a FOSS perspective, Metagoofil empowers individuals and communities with a CLI-based, no-tracking, surveillance-free method to gather public data for legitimate research and security review.
· · ─ ·𖥸· ─ · ·
Real-World Use Cases of Metagoofil Across Sectors
Whether you’re a digital rights advocate, policy researcher, or tech hobbyist, here’s how Metagoofil can support your work:
NGOs & Advocacy Groups
- Investigate exposed policy files: Quickly audit what documents an agency or entity has unintentionally exposed.
- Campaign intelligence: Gather public-facing PDFs that reveal strategy documents, grant releases, or outdated security policies.
Government Agencies
- Secure your own domains: Perform recon on your public infrastructure to identify sensitive documents left exposed.
- Compliance verification: Scan departmental websites to ensure no confidential data is unintentionally accessible.
Businesses
- Brand protection: Discover if internal documentation (product specs, presentations) is leaking through unsecured directories.
- Competitor analysis: Ethically gather public-facing content released by competitors to understand positioning or pricing strategy.
Students, Tech Enthusiasts & Bloggers
- Academic resource mining: Search university websites for research papers, syllabi, and lecture slides.
- Build recon workflows: Integrate Metagoofil into your OSINT lab to expand your toolkit alongside Maigret or Sherlock.
- Write data-backed content: Bloggers can uncover and reference PDF-based research in niche topics like law, healthcare, or tech.
💡
Pro Tip: Combine Metagoofil with ExifTool and Holehe to cross-reference authorship and leaked email patterns.
· · ─ ·𖥸· ─ · ·
How to Install Metagoofil on Ubuntu
Metagoofil is available on Kali Linux by default, but you can install it easily on any Ubuntu-based distro. Here’s how.
Step 1: Install Required Dependencies
sudo apt update
sudo apt install python3 python3-pip gitStep 2: Clone the Maintained Fork
git clone https://gitlab.com/kalilinux/packages/metagoofil.git
cd metagoofilStep 3: Install Metagoofil
If needed, install additional dependencies:
# Create a virtual environment to avoid OS headaches
python3 -m venv myenv
# Activate the virtual environment
source myenv/bin/activate
# Install metagoofil
pip3 install -r requirements.txtMetagoofil is now ready to use.
· · ─ ·𖥸· ─ · ·
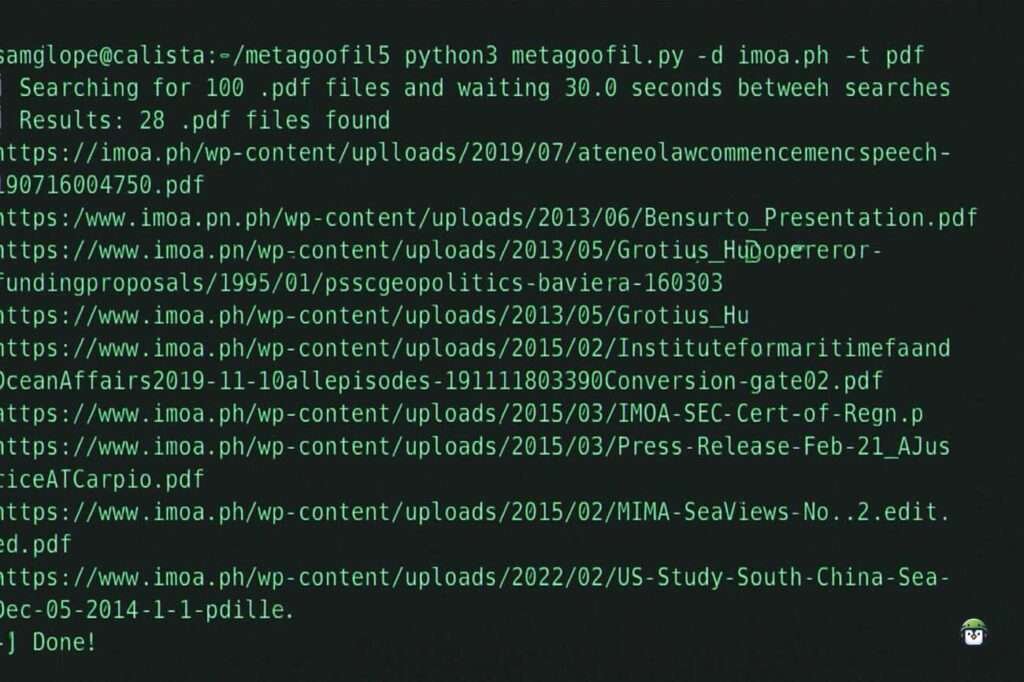
How to Search for PDFs Using Metagoofil
Here’s how you can start finding PDFs from a specific domain.
Step 1: Basic Usage Example
python3 metagoofil.py -d example.com -t pdf-d: Target domain-t: Filetype to search (e.g., pdf, doc, ppt)-l: Number of results-o: Output directory for the downloaded files
Step 2: Analyze Metadata (Optional)
Since newer Metagoofil versions skip metadata extraction, use ExifTool for deep document analysis:
exiftool -r output_folder/*.pdf | egrep -i "Author|Creator|Email|Producer|Template" | sort -u· · ─ ·𖥸· ─ · ·
Discover PDFs, Protect Data, and Think Like an Ethical Hacker
When you know how to search for PDFs effectively, you’re not just hunting files—you’re uncovering stories, policies, and sometimes, accidental leaks.
Metagoofil may no longer extract metadata, but it remains a quiet powerhouse for PDF recon, especially when paired with tools like wget and exiftool.
Whether you’re securing your org’s digital surface or learning the craft of ethical OSINT, this guide gives you the FOSS tools to do it right.
Subscribe now at samgalope.dev/newsletter to get more real-world, command-line recon tips—and keep your skills razor sharp in the age of leaks and breaches.
⚠️ Important: These tools are intended for ethical hacking, security research, and education. Use them only on systems and networks you own or have permission to test. Unauthorized use can lead to serious legal consequences.





Leave a Reply